Service Accounts on Google Cloud Platform
It often happens when I work with clients that they don't have much experience with Google Cloud Platform, i.e. they generally register and create project, add developers to project, but for example setting service accounts in not so straightforward in case they want to give developer granular access. So in this article I want to give an overview about Service Accounts which is often used feature in development on Google Cloud Platform and it's written in mind for non developers.
How to set up Service Account.
Common operations with Service Accounts.
What is Service Account?
Service Account is similar as normal user's account with difference that is generally used in code to access GCP products. Just as users can have different roles so does the Service Account. Data which is used to authenticate against GCP is provided as key (practically it's file either in json or p12 format) which can be then used in code. So as users are authenticated with email and password, service accounts are authenticated with key file. Because it's file it can be easily copied, shared etc and with that security of your project can be compromised so be careful where you store your Service Account files how you share them and where people with whom you shared them are using them and we're they keeping them.
Service Accounts management is under IAM & admin section
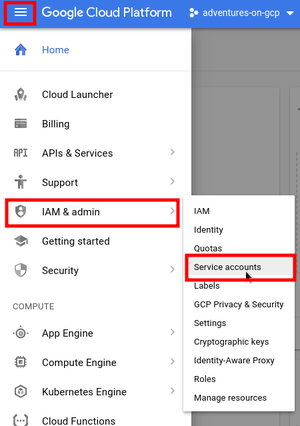
How to set up Service Account
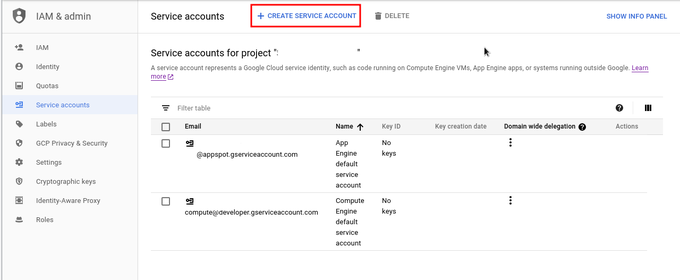
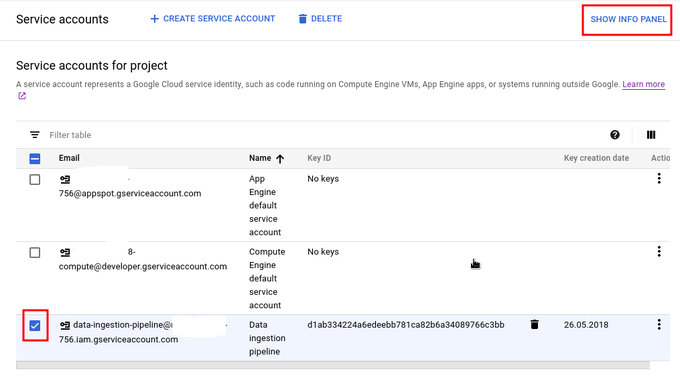
This is list of service accounts, as it can be seen on image bellow, there are 2 service accounts and we will create new one, to do that click on button CREATE SERVICE ACCOUNT.
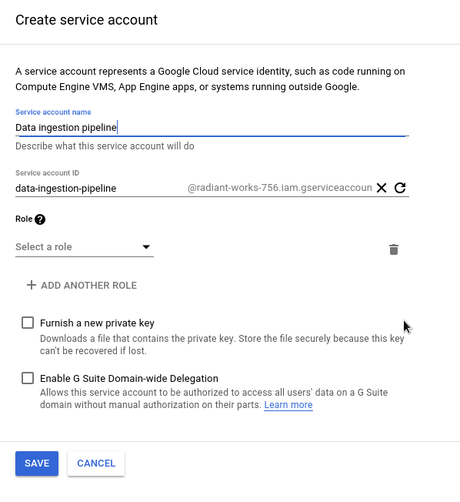
In popup window there are few things to set:
- Service account name - this is just name which will be displayed, so give it some meaningful description especially if you will have multiple accounts to easily navigate. In this case I'll hypothetically want to create some script or service which will run on server and get data from third part API, upload to Cloud Storage and then upload to BigQuery.
- Service account ID - initially this is derived from service account name, but you can change if you want, technically it's not so important.
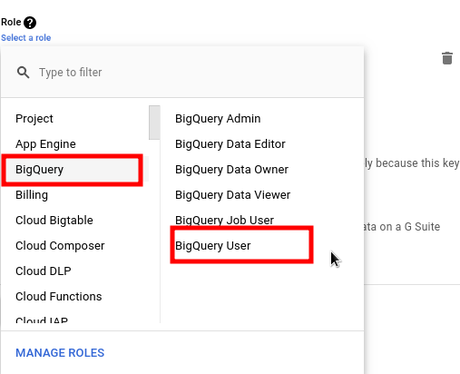
- Roles - here you can define multiple roles for this service account. In this example I'll add roles for BigQuery and Cloud Storage. Naturally all those roles are maybe not easy to understand and I guess best resource is this comprehensive article where all possible roles are exaplained https://cloud.google.com/iam/docs/understanding-roles.
When you click on Select a role field, small window will pop up with list of products and it's roles.
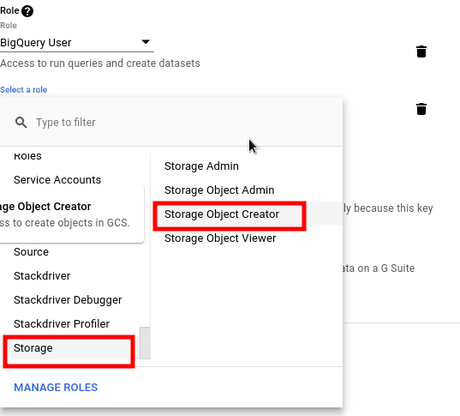
Last thing is to check option Furnish a new private key with which when you will hit SAVE button, json file will be downloaded.
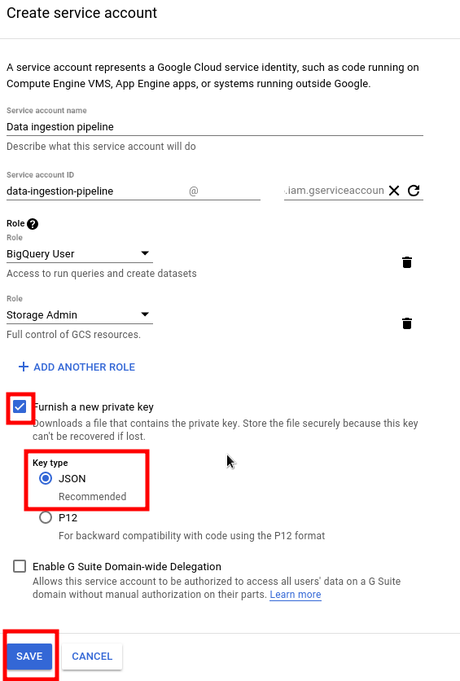
Message after creation.
This is how content of service account file key looks like.
{
"type": "service_account",
"project_id": "just-some-project",
"private_key_id": "e5703451d59c7f1152517122a9e8824",
"private_key": "-----BEGIN PRIVATE KEY-----\nMIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQCgGPVstF25mezs\nSrIQ+jW0neRqEaCi3800d5Sm5F36cq2vTl9kFkahz4zmQiyNqgyBayQbipHJxVV0\nfeI65nh+BXj4nX2ZC1vLGRIlcRwzauW/58wcMAtaTPRstXwk/LkJJURG1klSF+kD\np3bD6VzpE5nJt396jy0g7q/Mlh/gGNzTS05BsWHl4+iurtlqCzB5XKiKpDlF9CC8\nsa/tAvex1mCuUgjZKcMMpqSOuVVFQeyk9xx6TO3GbQfYvHPwpZBrEY14Aplw2Ikg\n4qiQHBVSBACA9LHRTRHYGmwvrAYx7sWQk8WI9Q/oN5xzZOp5rrWJGl1XZxlryLKL\ntOTQPCFPAgMBAAECggEAB4t1kXRkkFkdLbuNbbhk7IieWZNQFyzl3kmeY0kS1rkt\nzzupyi00ke6WjMlkkR6I7VZvwq6ClVgr4UwHa9AtsH6wh0LgxuQepNEfJk2QzymD\n/0m8uD1ZY52JzU+2NIYGcFRlxdLWbLx8ujPbqHroaoGGd1ei9dMmhM1K0qDmiqh+\nL6xhEoujxySgYobDk5ZZt3EbG1N6N4D+C+/6mguakXKU2nl7kyEGngykOij67L+C\nnnK/4R4HHUNU5YOTriq+7WYNwMOzHrVT5z41+0yG3FJvIZ0Iy57x5RNw5xVHoYNn\niX8m7jLQ/ByHCeJ9HcqUdIj3ovkvtTS2zsozaCiVHQKBgQDVsKwBp8KbgaC9xluY\nNuN88t/m6SPvBn9k4xaLnvQkjCO/LKOlRsxSPzmxzTc7lOocVXsr7IyzoDH4QMpo\nyjbajjqvcUG2L2oE1iG9nKLtTC2iaeR/OPJRRagvPhgPe8cskqy/I60tlfvgr7kB\nzRftCcJXTI3J94gFzd0tnEB9awKBgQC/y9U9MLrm0aQk9+VWJDMn9X0/6qSXaxRK\nDOlijUjWSvGPOZ+hetueDZnZyBSjuFjcX8hV2qMn2TDPnd/KxGxhuB8Xe6ExTWnT\nB6SHT3BpG6+4u9atuoSUY6AYGbFCP2v7jf2FTPXoAn\nC2Z+XuND4t7wlxxIDxRzaBx95wwmEkrm0A2uNcpy1z2kPYGKS/U8blnGC8ie7anT\ng89mor9s2Vkno6rJ+r0nOtzy\n-----END PRIVATE KEY-----\n",
"client_email": "[email protected]",
"client_id": "109097848740185",
"auth_uri": "https://accounts.google.com/o/oauth2/auth",
"token_uri": "https://accounts.google.com/o/oauth2/token",
"auth_provider_x509_cert_url": "https://www.googleapis.com/oauth2/v1/certs",
"client_x509_cert_url": "https://www.googleapis.com/robot/v1/metadata/x509/data-ingestion-pipeline%40r756.iam.gserviceaccount.com"
}
As I wrote earlier, downloaded file is used in client libraries to access GCP services. Of course it's at most importance to keep this file secure because who ever gets this file can have access to your GCP products or access data based on permissions and roles which are granted to that Service Account.
Common Operation with service accounts
In the list of Service Accounts.
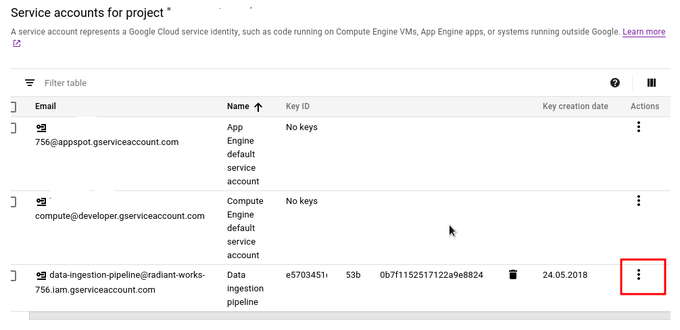
When you click on settings you get options to Edit, Delete and Create Key
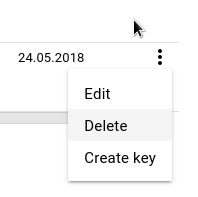
Edit - gives you just possbility to just change Service Account Description
Delete - deletes Service Account
Create Key - this furnishes new key / file. This means that you can have multiple keys / file for one service account. Clicking on trash bin you can delete them. In case you thing key / file has been compromised, that's the first thing you should do.
Other common thing is to modify Roles assigned for Service Account.
When you go to IAM section you will see list of account including user and service accounts. Now depending on the screen resolution you may want to move at the bottom slider to the right to get to options :).
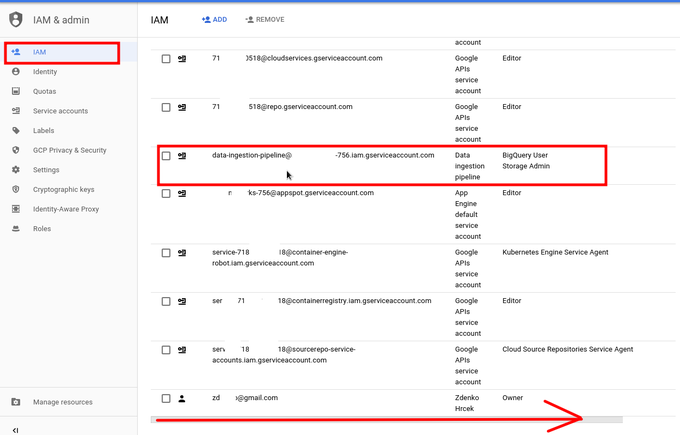
You can see Roles assigned and options to edit or delete Roles.
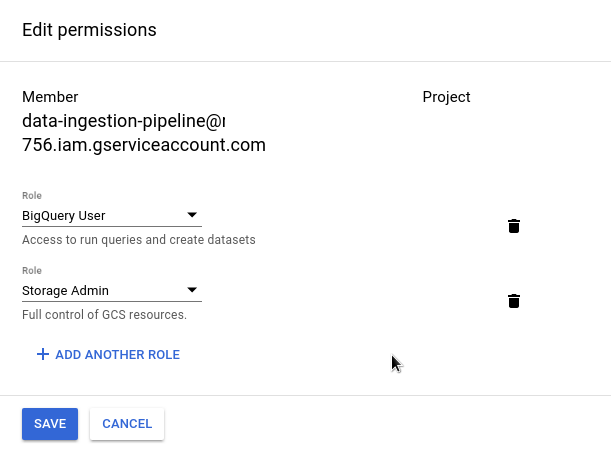
When you clink on pen (Edit) you can delete, change or add Roles similar as during creation.
Last feature of Service Accounts that I want to include here is assigning access to Service Accounts. Basically when you create Service Account, you can assign to it access for one or multiple user accounts. With this feature you can selectively grant access for developers to Service Accounts without giving them general access to all of them. When they have access to service account, they can modify it, change roles etc.
To assign user to Service Account, go to Service Accounts list, check Service Account for which you want to assign access, and then click on top right corner SHOW INFO PANEL.
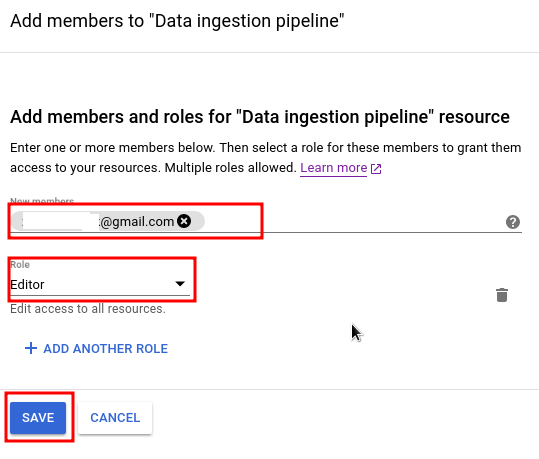
In pop window to assign user, you need to enter user's email (you need to also click on it) and select one or more Roles. Here there are only 3 group of roles: Project, Service Accounts and IAM and when selected, they will be only applied for this Service Account, not the whole project.
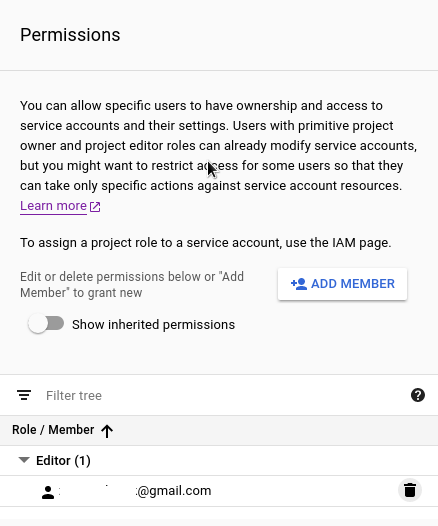
After adding you can see grouped Members under Roles.
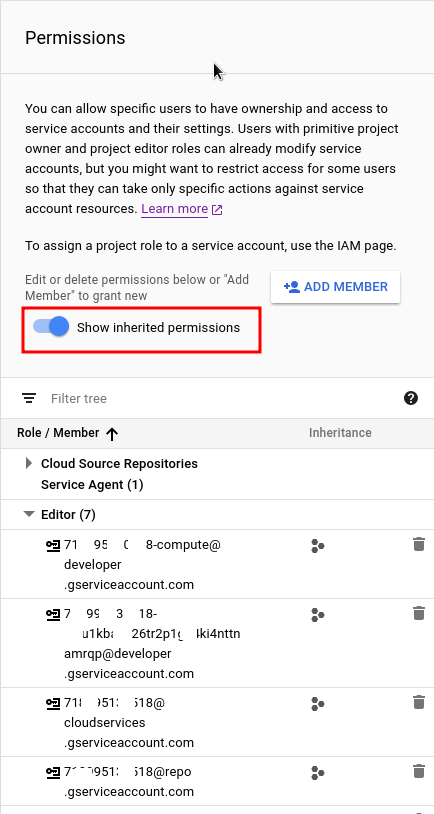
When you switch Show inherited permissions you can see also inherited permissions, i.e. Members with Roles which have implicitly access to this Service Account.
I hope this article has given you clearer overview of what Services Accounts are and how to handle them.